Have you ever imagined booking a bus ticket for free or at the lowest cost and traveling anywhere you want? Sounds unbelievable, right? Well, today, I’m going to share an interesting and impactful security bug I recently discovered in a government transport application.
What is TNSTC?
The Tamil Nadu State Transport Corporation (TNSTC) is one of the largest public transportation providers in Tamil Nadu, India. It offers affordable bus services across the state and neighboring regions, serving millions of passengers annually.
Revenue in Recent Years:
- 2021–2022: TNSTC recorded a total revenue of ₹902.55 crores, marking a 12.48% increase from the previous year.
- 2022–2023: The Tamil Nadu Transport Department collected a whopping ₹6,674 crores, achieving a 34% growth in revenue.
- Post-Diwali 2024: The Kumbakonam division alone generated ₹17.1 crores in revenue by operating special bus services.
Given the scale and importance of this service, ensuring its application is secure is a critical responsibility.
Introduction
Hi, I’m Karthikeyan V, a security researcher passionate about testing and securing applications. I regularly participate in Vulnerability Disclosure Programs (VDPs) offered by organizations like IndGov, BBC, UKgov, and more.
As someone who travels frequently, I usually book bus tickets using TNSTC. One day, I decided to test the security of their Android application as part of my research. What I found left me both amazed and concerned.
Setting Up My Research
This time, my focus was on the Android application of TNSTC. To perform dynamic analysis, I used Genymotion (an Android emulator) along with Burp Suite to intercept the app’s HTTPS traffic. After a few minutes of setup, I successfully configured the app to route its traffic through Burp Suite for testing.
As usual, I started with common areas like authentication and session management. Then, I shifted my focus to the ticket booking and payment functionality.
The Discovery
While analyzing the app’s HTTP requests, I noticed that the POST request contained a parameter reflecting the ticket price. As a regular bug hunter, I instantly recognized the possibility of parameter tampering.
Here’s what I did:
- I modified the ticket price value in the intercepted request using Burp Suite.
- Instead of the actual ticket price (₹750), I replaced it with ₹1 and submitted the request.
The result? A successfully booked ticket for just ₹1!
To confirm the success, I checked the generated ticket, and it displayed the original price (₹750), but the payment processed was only ₹1.
Boom! This proved the application was vulnerable to parameter tampering, which could allow malicious users to book tickets at a fraction of their actual cost.
Responsible Disclosure
Understanding the critical impact of this vulnerability, I immediately reported the issue on 21st December 2024 to IndGov, providing a detailed report with a proof-of-concept (PoC) video.
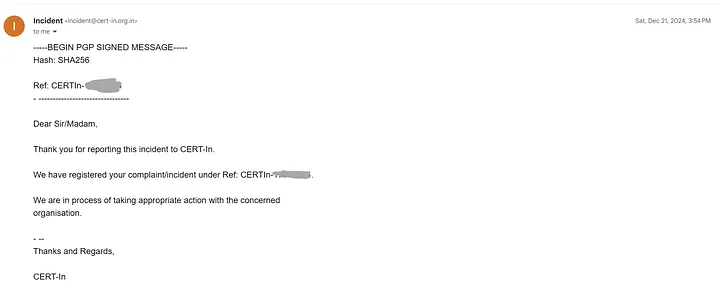
I promptly received an automated response acknowledging my submission, and I’m hopeful they will address this issue soon to secure the application.
Not Just One Bug!
This was not the only issue I discovered on that day. I also found and reported another critical bug in the same application. I’ll be sharing the details of that discovery in another write-up soon, so stay tuned!
A Note on Ethical Hacking
I’d like to emphasize that this research was conducted ethically:
- I only performed the booking to create a PoC and did not exploit or use the ticket maliciously.
- I have not disclosed any sensitive details, such as the POST request endpoint or application-specific data, in this write-up.
- My intent has always been to help secure government applications and protect users.
Conclusion
As a security enthusiast, I feel proud to contribute to the safety of applications that millions of people rely on every day. This experience has reinforced my commitment to ethical hacking and responsible disclosure.
LEARN MORE — PROFESSIONAL COURSES
If you want hands-on training (mobile & web bug bounty and API Bugbounty / VAPT), check out our certified courses — real apps, real bugs, live labs.

🔥 Limited-Time Offer: ₹5,500 course now at just ₹2,500!
Enroll / Learn more: https://university.cappriciosec.com/CMABP.html

🔥 Limited-Time Offer: ₹7,999 course now at just ₹4,999!
Enroll / Learn more: https://university.cappriciosec.com/CWBP.html

🔥 Limited-Time Offer: ₹7,999 course now at just ₹5,999!
Enroll / Learn more: https://university.cappriciosec.com/CAPBB.html
What you get
- Live, hands-on pentesting on real applications — not simulated labs.
- Comprehensive curriculum — web & mobile security fundamentals, OAuth, redirect handling, PKCE, secure coding and remediation guidance.
- Real-world case studies (responsibly redacted) and POC walkthroughs.
- Career & bounty guidance — report writing, disclosure, and monetization of findings.
- Final certification & lifetime access to recordings.